Free Coaching Lectures - Free Railways Coaching Lectures | Free SSC Coaching Lectures | Free RRB Coaching Lectures | Free Government Exam Coaching Lectures | www.ConceptsMadeEasy.com

Use this Coupon to get upto 70% OFF on Hostarmada Affordable Cloud SSD Web Hosting Services
Following are the list of best awaresome videos on "Mruvmqyu') Or 621=(select 621 From Pg_sleep(15))" which you can watch online here or download.
 15 MCQ Questions with Explanation 🥸 || MS SQL Server Injection 🧐|| MS SQL Server Bulk operations🥹
15 MCQ Questions with Explanation 🥸 || MS SQL Server Injection 🧐|| MS SQL Server Bulk operations🥹
What operation cannot be performed in bulk? Under the which recovery model, all bulk operations are fully logged. DOWNLOAD
 PostgreSQL REGR_AVGY() Function | REGR_AVGY in PostgreSQL | PostgreSQL REGR_AVGY() Tutorials
PostgreSQL REGR_AVGY() Function | REGR_AVGY in PostgreSQL | PostgreSQL REGR_AVGY() Tutorials
In this PostgreSQL tutorial, I have explained how to use the PostgreSQL REGR_AVGY() Function to calculate the average of the ... DOWNLOAD
 SQL Injection - Lab #7 SQL injection attack, querying the database type and version on Oracle
SQL Injection - Lab #7 SQL injection attack, querying the database type and version on Oracle
In this video, we cover Lab #7 in the SQL injection track of the Web Security Academy. This lab contains a SQL injection ... DOWNLOAD
 How To Select Database In PostgreSQL Using pgAdmin and SQL Shell psql || PostgreSQL Tutorials
How To Select Database In PostgreSQL Using pgAdmin and SQL Shell psql || PostgreSQL Tutorials
knowledge360 #akramsohail #akramsohailproject You Are Hearty Welcomed To My Channel Knowledge 360. Here I post ... DOWNLOAD
 PostgreSQL REGR_AVGX() Function | REGR_AVGX in PostgreSQL | PostgreSQL REGR_AVGX() Tutorials
PostgreSQL REGR_AVGX() Function | REGR_AVGX in PostgreSQL | PostgreSQL REGR_AVGX() Tutorials
In this PostgreSQL tutorial, I have explained how to use the PostgreSQL REGR_AVGX() Function to calculate the average of the ... DOWNLOAD
 SQL Injection - Lab #3 SQLi UNION attack determining the number of columns returned by the query
SQL Injection - Lab #3 SQLi UNION attack determining the number of columns returned by the query
In this video, we cover Lab #3 in the SQL injection track of the Web Security Academy. This lab contains a SQL injection ... DOWNLOAD
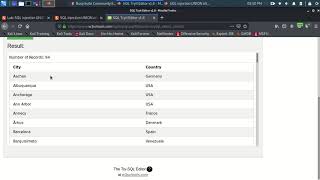 sql injection union attack determining the number of columns returned by the query | portswigger lab
sql injection union attack determining the number of columns returned by the query | portswigger lab
This lab contains an SQL injection vulnerability in the product category filter. The results from the query are returned in the ... DOWNLOAD
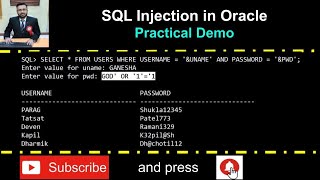 SQL Injection in Oracle with Practical Demo
SQL Injection in Oracle with Practical Demo
Warning: Purpose of this video is to demonstrate SQL Injection practically and it is for education purpose only. It is strongly ... DOWNLOAD
 SQL injection attack, querying the database type and version on Oracle | Web Security Academy
SQL injection attack, querying the database type and version on Oracle | Web Security Academy
Web Security Academy Lab: ... DOWNLOAD
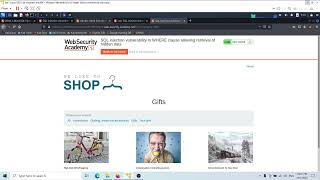 Lab: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
Lab: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
This lab contains an SQL injection vulnerability in the product category filter. When the user selects a category, the application ... DOWNLOAD
 Dangerous Codes: SQLi
Dangerous Codes: SQLi
short #infosec #sql #sqlinjection. DOWNLOAD
 Basics of SQL Injection - Penetration Testing for Ethical Hackers
Basics of SQL Injection - Penetration Testing for Ethical Hackers
SQL injection is a common hacking technique used to retrieve or destroy data from a database without permission. It is considered ... DOWNLOAD
 SQL injection attack, listing the database contents on Oracle
SQL injection attack, listing the database contents on Oracle
Lab: SQL injection attack, listing the database contents on Oracle PRACTITIONER This lab contains an SQL injection vulnerability ... DOWNLOAD
 SQL injection attack, querying the database type and version on MySQL and Microsoft
SQL injection attack, querying the database type and version on MySQL and Microsoft
This lab contains an SQL injection vulnerability in the product category filter. You can use a UNION attack to retrieve the results ... DOWNLOAD
 PostgreSQL Security Features: Episode 6 - SQL Injection Attacks
PostgreSQL Security Features: Episode 6 - SQL Injection Attacks
An SQL #injection attack is an attempt to compromise a database by running SQL statements that provide clues to the attacker as ... DOWNLOAD
 SQL Injection - Lab #3 SQLi UNION attack determining the number of columns returned by the query
SQL Injection - Lab #3 SQLi UNION attack determining the number of columns returned by the query
In this video, we cover Lab #3 in the SQL injection track of the Web Security Academy. This lab contains a SQL injection ... DOWNLOAD
 What is a SQL Injection Attack? - The Complete Python/PostgreSQL Course 2.0.
What is a SQL Injection Attack? - The Complete Python/PostgreSQL Course 2.0.
What is a SQL injection attack? How does it happen? How can you stop it?! Find out now in this lecture from Jose Salvatierra\'s ... DOWNLOAD
 7.6 - Postgres Administration - Error Logs
7.6 - Postgres Administration - Error Logs
Postgres error log file, Troubleshoot postgres errors. DOWNLOAD
 Sql Injection Attack, Querying the Database Type and Version on Mysql and Microsoft (Audio)
Sql Injection Attack, Querying the Database Type and Version on Mysql and Microsoft (Audio)
This Video Shows the Lab Solution of an SQL injection vulnerability in the product category filter. You can use a UNION attack to ... DOWNLOAD
 SQL Injection | Complete Guide
SQL Injection | Complete Guide
In this video, we cover the theory behind SQL injection vulnerabilities, how to find these types of vulnerabilities from both a white ... DOWNLOAD